USE CASES

Malware Detection
Malware is the top reason why your devices might get hacked. There are different kinds of malware like Trojans, worms, and botnets. Cybercriminals and hackers use these to infect devices and do bad stuff like spying on other devices, connecting to control centers, sneaking in through hidden entrances, spreading to other devices, and getting more control over systems. Zero-Day malware and Ransomware are especially scary because they can cause big problems without warning, messing up operations and costing a lot of money for all kinds of businesses.
Challenges
- Devices outside of a company’s protective barrier, like the firewall, are vulnerable to harmful websites or downloading from places like torrents, which can bring in malware.
- Malware can be tricky to spot because it can hide using methods like obfuscation and stealth mode.
- As time goes on, the ways that malware gets into systems change, making older defenses useless. This includes things like relying on signatures or trying to predict malware based on patterns.
Shield 24×7’s Solution
Malware tactics and techniques have evolved to avoid detection by software tools (system maintenance) and security controls (whitelisting/blacklisting). Sophisticated methods (including ML and AI) are used to overcome advanced detection techniques. This leaves very little to guesswork and static rules. Shield 24×7’s solution (both aiSIEM and aiXDR), however, relies primarily on behavioral patterns across users and entities while questioning suspicious processes, file changes, connections, scans etc, while keeping eyes and ears open to the external world of Cyber Threat Intelligence. This mode of staying on the toes aided by ML and AI imparts aiXDR and aiSIEM the ability to catch Zero-Day Threats, Ransomware and other malware variants with high degree of confidence.
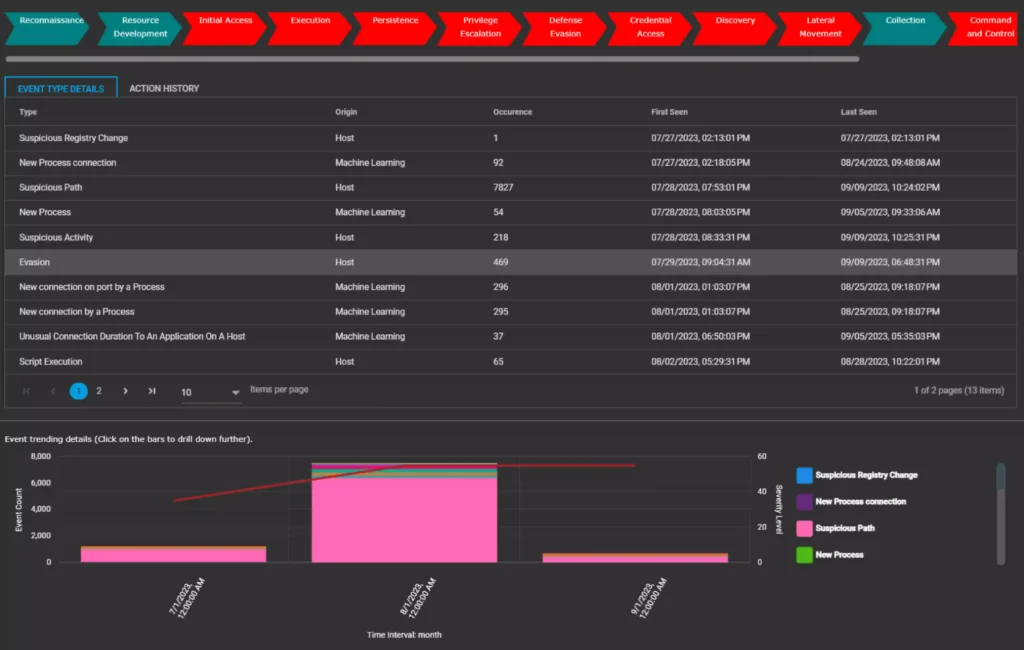
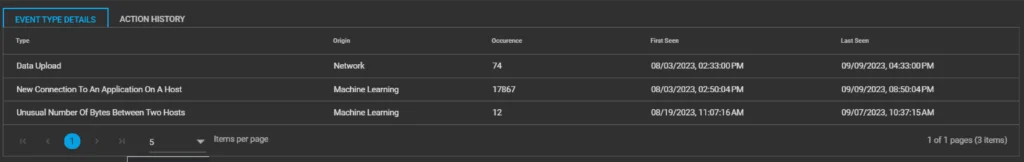
When drilling down, we get a granular picture with different types of Threat Indicators and number of instances associated with each indicator.
Threat Indicator Type | SIEM Tactics Used By Malware Detection |
New process connection. | New processes (executables) were detected attempting to set up connection with Public IP addresses from particular host (say, Alpha-Y). |
Process seen on a new host. | Several suspicious processes were detected on the host Alpha-Y. |
New process. | Several new processes with suspicious hash (based on Threat Intelligence sources) were detected on Alpha-Y. |
Suspicious process detected. | Several suspicious processes were detected with unusual parent processes on the host Alpha-Y. |
Evasion. | Several instances of suspicious parent processes were detected that are used by attackers or malware masquerading as legitimate Windows processes. |
Windows exploit. | Multiple suspicious child processes related to Windows logon scripts(users or group of users) detected on host Alpha-Y. These scripts are used to perform administrative functions, often executing other programs or sending information to an internal logging server. |
New connection by a process. | More new connections detected on the host Alpha-Y. |

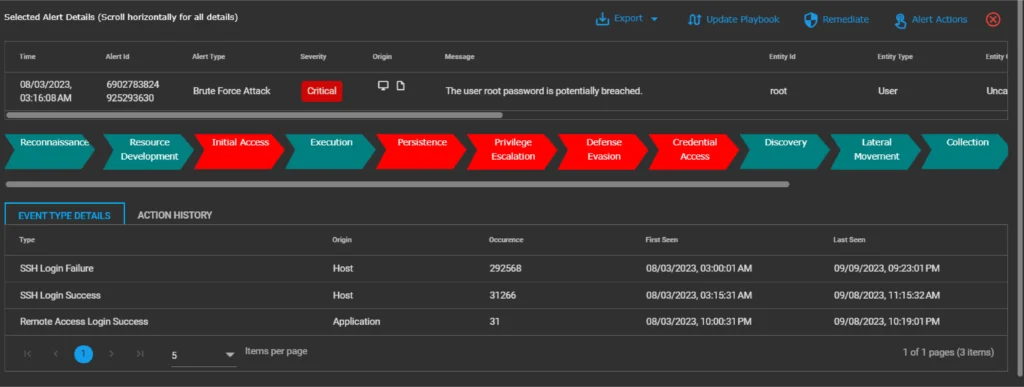
Brute Force Attack
In a Brute Force Attack, the bad guys keep trying different combinations of usernames and passwords until they get in, and they do it in a way that’s hard to notice. Sometimes, they use a tactic called Password Spraying, where they try common passwords like “password” or “Password123” on lots of different accounts. They might also use passwords they found on the dark web to break into other accounts, especially if people use the same password for everything. This is called Credential Stuffing.
Challenges
- Attackers can quietly get into a computer and launch attacks that don’t rely on being online, making them harder to find and stop.
- If people aren’t careful about creating strong passwords and keeping them safe, it’s easy for attackers to guess them and get in using a Brute Force Attack.
- When people connect to apps and servers without secure methods like VPN or strong SSL, it’s easier for attackers to exploit these connections online.
Shield 24×7’s Solution
For a good solution, it’s important to start from a standpoint of not trusting anything and use information about what’s happening right now and how people usually act to spot attacks. Shield 24×7‘s solution looks at things like where someone is, their IP address, what time it is, what device they’re using, how often they usually log in, and if they’re breaking any rules. It also uses fancy computer learning to watch for strange behavior. For example, it checks if someone is logging in from a new place, making a new connection, or giving new commands, which could mean someone is trying to break in using stolen credentials.
Additional scenarios of Brute Force Attack tracked and detected by Shield 24×7’s solution (both aiSIEM and aiXDR):
- Many times someone tries to log in but fails, whether from one or more places, inside or outside the organization, using one or more usernames.
- Failed logins from new places or new devices.
- Lots of times an account gets locked.
- Someone tries to guess passwords over and over to break into accounts with easy passwords.
Shield 24×7’s solution does more than just warn you about these attacks. It also helps stop them by telling firewalls to block the internet addresses where the attacks are coming from or by shutting down the user’s access.

Insider Threat
Sometimes, people working inside a company can become a danger, either on purpose or by accident. They might access private or important company information, like business secrets or patents, even if their job doesn’t require it. Sharing this info with someone who shouldn’t have it or using it for themselves can really hurt the company, both financially and in other ways. And then there are employees who are unhappy and do bad things like stealing passwords, sharing secret info, or deleting important data.
According to the Ponemon Institute Global Report in 2020 (Cost of Insider Threats), the average cost of insider threats worldwide went up by 31% between 2018 and 2020, reaching $11.45 million. And during that time, the number of these incidents increased by 47%.
Challenges
- It’s often hard to tell if someone inside a company is doing something wrong because we naturally trust our coworkers, and their actions might not break any rules set by the company.
- We can’t always predict or control insider threats with strict rules because they can happen unexpectedly.
- For example, if someone with permission checks business info while traveling or working odd hours, it might not mean they’re doing anything suspicious.
Shield 24×7’s Solution
Shield 24×7 uses a method called User Entity Behavior Analytics (UEBA) with Machine Learning to detect insider threats. This helps identify different tricks used by people causing trouble from inside the company.
- When someone’s login details are stolen or compromised, it’s a sign that an insider might be trying to access information they shouldn’t. For example, if a user logs into an unexpected place, which is different from their usual behavior, it could mean trouble. This can be seen in the screenshot below from the aiSIEM Portal.
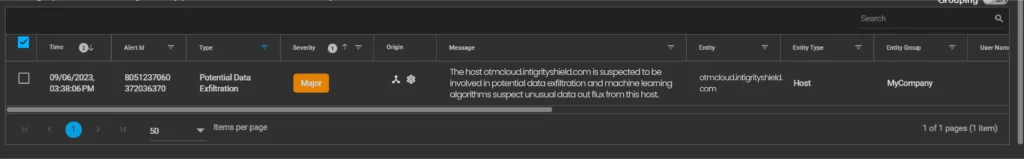
- Insiders might also try to take information out of the company, which is called data exfiltration. If there’s a lot more communication than usual with an important part of the company, it could mean this is happening. The methods used for detecting this are similar to those used for detecting data breaches.
In both cases, the system would send an alert of either major or critical importance, along with suggestions on what to do next.

Data Breach Detection
A data breach, also known as data theft or exfiltration, is when bad actors infiltrate an organization’s digital data. This can include anything from personal information to sensitive business data or intellectual property. These attackers might have various motives, like trying to make money by selling customer data, financial information, or personal identifiers on the dark web. They could also be aiming to damage the reputation of a specific organization, business, or even a whole country.
Challenges
- Detecting data exfiltration is tough because it looks like regular data traffic and can slip by unnoticed.
- The usual security methods, like DLP (Data Loss Prevention), often give lots of false alarms, which are costly to deal with and slow down users’ work.
- Usually, we only notice data exfiltration after a lot of harm has already been done. For instance, it took Equifax 75 days to realize they’d been breached.
Shield 24×7’s Solution
Detecting data breaches involves looking at various security-related information, like how files are being used, what users are doing, and the flow of data through the network (like which applications and servers are involved). It’s also important to consider any threat intelligence and the results of vulnerability scans, especially if outsiders might be involved.
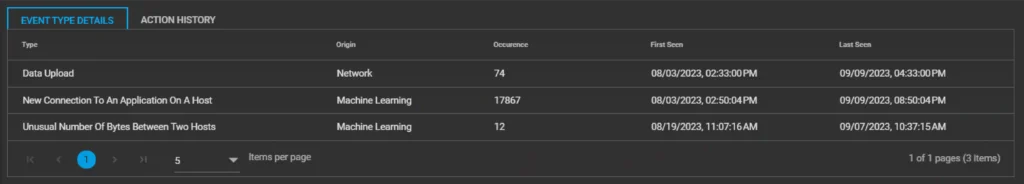
Shield 24×7‘s solution looks at all these pieces of information and uses machine learning to establish a standard pattern of behavior, so it can spot any unusual activity with confidence. This means it can pick up on things like a port scan that might indicate a breach is about to happen. By catching these signs early, it helps to limit the damage a breach can cause, which saves organizations both money and their reputation. Below is a screenshot from the aiSIEM Portal showing an alert about a particular computer involved in data exfiltration.
After looking more closely at the warning signs of a threat, we discovered that one computer is connecting to another computer (called a server) and a specific program. They’re exchanging information (bits of data) and, in the end, sending data to a public program.

Vulnerability Exploits
Attackers search for weaknesses in digital systems to get into a computer or server. Their goal is usually to install harmful software like viruses, trojans, worms, or bots. As malware evolves, attackers might try to learn more about the network by looking around inside it before connecting to a Command & Control Center. If they find a way in, like an open port, they can easily set up a way to talk to the Command & Control Center and send data out to a specific server.
Challenges
- Deciding which vulnerabilities to fix first is a big challenge, especially for big companies with lots of them.
- Fixing a security problem can take a long time, sometimes weeks or months, especially when there’s not enough security staff and lots of other tasks.
- It’s hard to tell if a plan to manage vulnerabilities is working well because its success depends on keeping security tight all the time, which is a tough job.
Shield 24×7’s Solution
Since there are lots of weaknesses in IT systems, we have to watch out for any attacks. Shield 24×7‘s solution looks at different signs of danger to decide if there’s a serious problem, like someone exploiting a vulnerability or attacking a website.
- A Vulnerability Exploit often starts with scanning the network to find servers with certain open ports. After that, the malware might connect to a public IRC server.
- A Web Exploit happens when a bad website tries to get too much information through a weird web address.
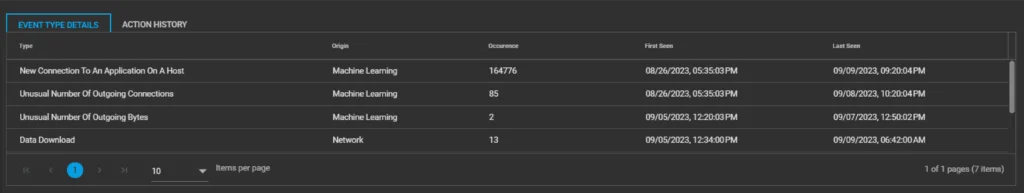
Screenshot (aiSIEM Portal) of a Vulnerability Exploit alert below shows a particular host conducting rigorous network scanning.
When we dig deeper into the warning signs, we see a bunch of different activities happening. There’s scanning ports, trying to access blocked apps, sending out weird data, and moving files around. Shield 24×7‘s OTM Platform uses Machine Learning and Artificial Intelligence to spot all these signs automatically.

Web Application Security
Web applications are often made to serve specific purposes, like supporting a business goal or partner program. But sometimes, they’re not built following the best coding rules and practices. Sometimes, they even use client-side code (like JavaScript) in ways that the company’s security can’t control.Bad actors try to get into web applications to do bad things, like stealing data or making users go to dangerous websites. It’s especially bad if they can get into important systems like ERP, CRM, or HRM through a web interface.Many major cybersecurity attacks and breaches happen through web applications. These include things like Cross-Site Scripting, SQL Injection, Directory Traversal, Remote File Execution, and Cross-Site Request Forgery. In fact, 9 out of 10 cyber attacks target web applications.
Challenges
- Many freelance web developers don’t know much about keeping websites secure, especially when using common tools like WordPress.
- It can be expensive to use all the tools needed for strong defense, like firewalls, scanners for finding weaknesses, and tools to spot and fix threats.
- People often trust applications and APIs they use for things like data analysis and business tasks in the Cloud, even though they might not be totally safe.
Shield 24×7’s Solution
As Web Applications continue to pose a major cyber security risk to organizations, Shield 24×7’s solution (both aiSIEM and aiXDR) is capable of detecting various indicators of attack vectors categorized as event type “Web Exploits”.
- Cross-Site Scripting (XSS) Attack happens when someone puts bad code into a text box on a website. This code can make you go to a bad website that tries to steal your personal info.
- SQL Injection Attack is when a bad person messes with a website by putting something unexpected in a text box. This lets them change stuff in the website’s database.
- Remote File Execution is when a bad person tricks a website into running a bad program that they put there earlier.
- Local File Inclusion is when a bad person uploads a bad program to a website. Then, they can make the website run this program.
Directory Traversal is a sneaky trick bad people use to look at stuff they’re not supposed to on a website. They use a trick that lets them see things like user lists and secret info.
Continuous Compliance
Ensuring that a company follows the rules set by regulators is an important part of its security plan. This means making sure the company’s policies match what the regulations require, getting official confirmation, and avoiding any penalties.
Usually, proving compliance has been a one-time thing. But we also need to be aware of the risk of not staying compliant. What if a company was following the rules on one day but not the next? Plus, keeping up with regulations is tough, making it hard for companies to stay secure and keep everyone involved safe. So, it’s really important for a company to always follow the rules. And it’s also important for them to be able to adapt easily as the rules change and new ones come out.
Challenges
- Compliance laws are becoming stricter, with hefty fines for those who don’t follow them. Governments, states, and regions are introducing new laws to hold organizations accountable for handling people’s personal data.
- Businesses are spending a lot of money, time, and effort to meet these compliance requirements. They often have staff dedicated to managing compliance tasks.
- If a business doesn’t comply with these laws, it can’t expand or operate in different areas as easily.
Shield 24×7’s Solution
Compliance is observed across different areas of Shield 24×7’s aiSIEM and aiXDR products.
- Logs are kept in their original form with timestamps and audit information. This helps maintain a clear record of events, which is important for meeting regulatory requirements and conducting forensic investigations.
- You can create and enforce various custom rules for accessing data, such as allowing, limiting, or denying access. This helps ensure security and compliance standards are met.
- Access to Shield 24×7‘s aiSIEM and aiXDR Portal (a graphical user interface) is managed through different roles to limit what users can do, which is important for security and compliance.
- All user actions in Shield 24×7‘s aiSIEM and aiXDR products are logged, which helps with compliance and allows for thorough auditing.
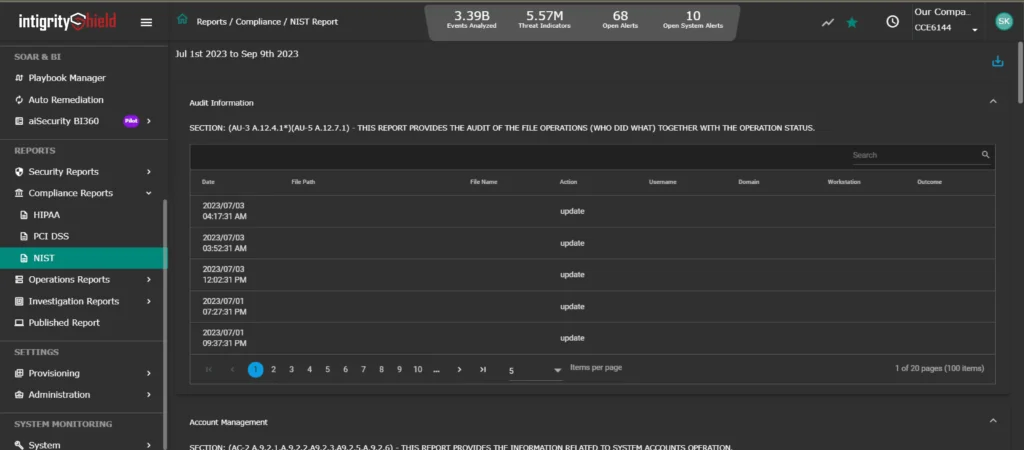
- You can generate reports regularly or whenever you need them to meet regulations like HIPAA, PCI-DSS, NIST, GDPR, and others. These reports help show that you’re following the rules (check out the example NIST Report below).
- Security Posture reports give you a visual look at how secure your organization has been over time, helping you see any changes or trends.
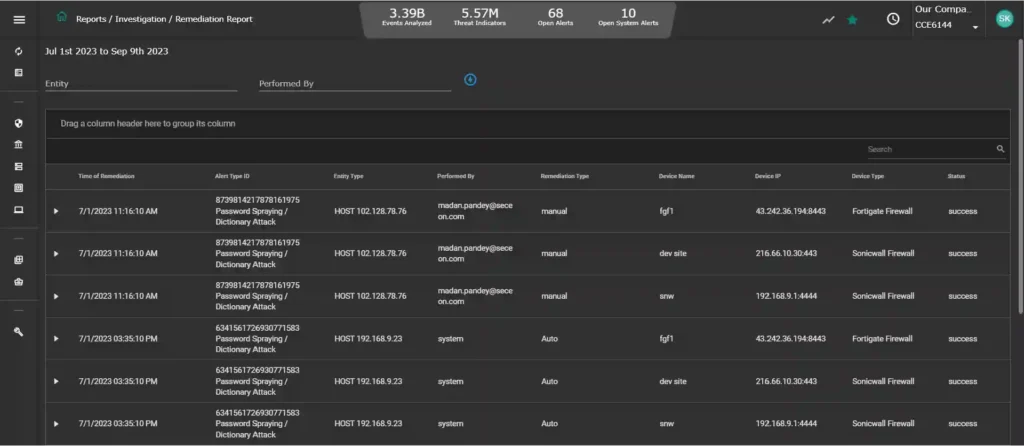
- Investigation reports, like ones on FTP or SMTP activity, go beyond what’s required by regulations. They help you fix issues and give additional information to regulatory bodies (see the example Remediation Report below).

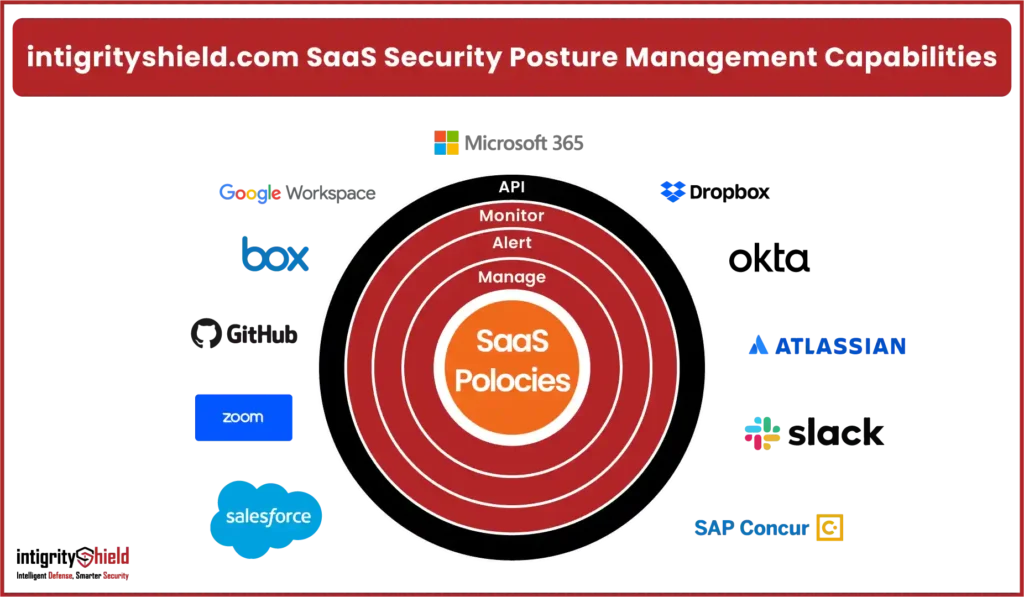
SaaS Security Posture Management
The fast move to using SaaS (Software as a Service) apps for more tasks in companies is making security, governance, and risk folks rethink how they work in this new setup. With 78% of companies keeping important info in SaaS apps, like personal data and financials, and the average mid-size company using lots of different SaaS apps, security and risk teams are having to set up specific controls and rules for each app.
This shift is happening because research from the Cloud Security Alliance found that most security problems (63%) happen because SaaS apps aren’t set up right.
Challenges
- Security teams need to see everything in one place: who’s using what, who has what permissions, what’s happening, and whether everything is set up securely across online tools. This helps them protect against dangers and attacks. They also need to connect security alerts from these tools with information from their whole system, like networks and users.
- Bad actors are increasingly targeting online tools used by companies. These tools aren’t always managed centrally, which means IT and security teams might not know what’s going on with them.
- People who manage these online tools in a company might not always know the best ways to keep them safe and working well.
- Teams responsible for making sure everything is done safely and according to the rules need to be sure that everyone is following the right procedures. If not, they need to know about it, keep a record of what happened, and if possible, fix it.
Shield 24×7’s SSPM Capabilities
- Shield 24×7 has created a way for customers to easily see what’s happening with security in some popular online tools. This helps security teams work better, saves money by organizing information neatly, and gives a full picture of what’s going on in their online spaces.
- When Shield 24×7‘s security features are used with supported online tools like Microsoft 365, Dropbox, Zoom, and others, it makes these tools safer to use for businesses. This makes it easier for teams to keep their work secure while still being productive and creative.
- Shield 24×7‘s systems are always watching for any problems with data security and will alert and stop any attempts to steal or share sensitive information.
- Customers can keep records of what’s happened in the past and use this information to respond to incidents, find threats, and check that everything is being done properly. Shield 24×7 also gives detailed reports on threats using a system called MITRE ATT&CK.
- Shield 24×7‘s platform works well with many security rules and can generate reports to show that everything is being done according to standards like NIST, GDPR, HIPAA, and others.
By using Shield 24×7‘s advanced aiSIEM platform, which is powered by real-time artificial intelligence and machine learning, security teams can better detect and respond to threats in their computer networks. This platform combines data from various sources like software services (SaaS), network activities, user actions, and device operations. It helps security experts work more efficiently and can even automatically respond to security issues if set up that way. This means less time and money spent on managing and organizing logs.
With Shield 24×7‘s support for SaaS applications, organizations can ensure that their security measures align with the needs of their users who rely on these applications. Additionally, using this platform gives them a clearer picture of potential threats and the individuals or groups behind them in both SaaS and cloud environments. Ultimately, it’s a way to strengthen security while still accommodating the use of SaaS tools.

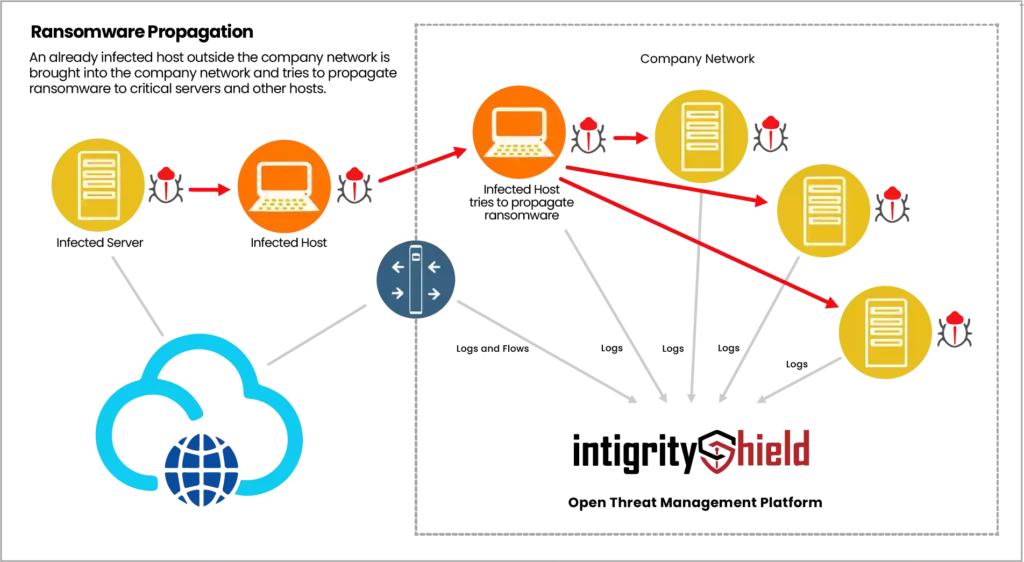
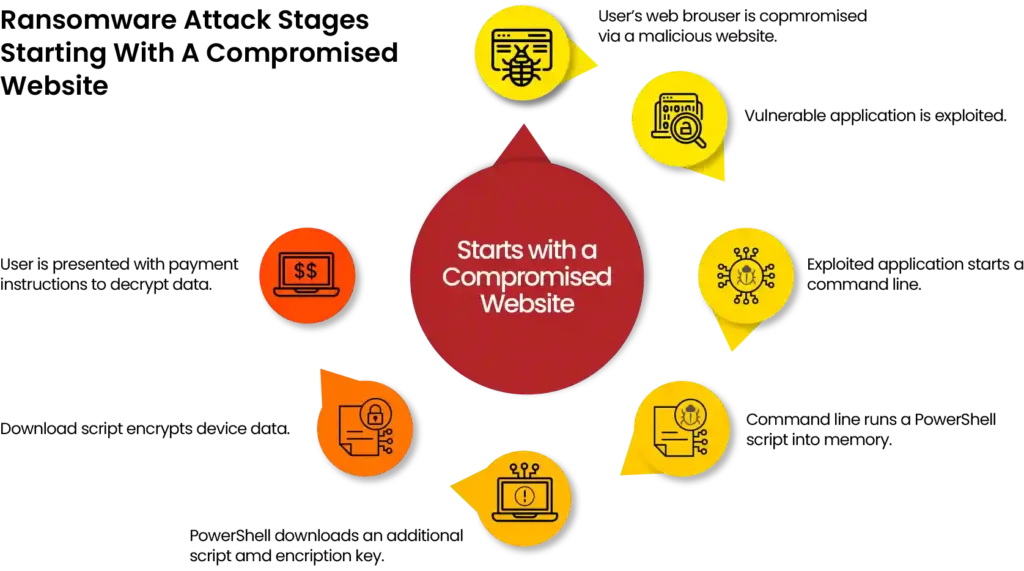
Ransomware Attack
In recent years, there’s been a steady increase in targeted ransomware attacks on various organizations, including government departments, local governments like cities or towns, schools, colleges, big companies, service providers, and even small to medium-sized businesses. Just like how computer viruses have changed over time, ransomware attacks have also evolved. They used to be pretty simple, usually just infecting one computer with important files. But now, they’re much more advanced. They can spread through a whole network, helped along by something called worms, which makes it easier for the attackers to hold more systems and demand more money.
These days, ransomware attacks often start with sneaky programs like Emotet, which can do things to avoid being caught and even delete backup files to make it harder to recover without paying up. Some of the most famous ransomware attacks include WannaCry, CryptoLocker, Ryuk, Petya, notPetya, and Maze. They’ve caused a lot of trouble and damage.
Challenges
When ransomware strikes, it usually happens in several steps. Each step might raise red flags that could signal an impending ransomware attack to different security systems. But, there are some challenges with using current security tools to spot and stop ransomware.
- More false alarms happen because each security tool can’t see everything, leading to alert overload.
- Sometimes, threats slip through because the tools aren’t connecting the dots between different signs of trouble.
- And it takes longer to react because we rely on skilled security experts to piece together all the clues and confirm an attack before doing something about it.
Shield 24×7’s Solution
To catch ransomware, we need to closely watch how it behaves and use models to predict its moves. But most traditional tools rely on human analysts to spot strange behavior and connect the dots between different signs of trouble. This puts a lot of pressure on the analyst’s expertise and ability to navigate complex interfaces, which can lead to subjective conclusions.In contrast, Shield 24×7‘s aiSIEM/aiXDR uses Machine Learning and Artificial Intelligence to do this job. It looks at patterns in behavior and automatically connects the dots between different signs of trouble. When it’s confident that there’s a problem, it raises an alert for the analyst to check out.
Here are the top 3 scenarios corresponding to Ransomware detection with Shield 24×7 aiSIEM and aiXDR.
Detection at Host: When ransomware tries to infect a computer, aiSIEM/aiXDR gets to work. For example, if it’s an email phishing attack, it checks the email server logs and looks at what’s happening on the computer to spot any strange or suspicious activity.
Detection at Host Connecting with C&C: The malware tries to talk to a Command and Control Center (C&C) from the infected computer. It might create a new web address and try to connect there. In this stage, Shield 24×7’s aiSIEM/aiXDR steps in to find these new web addresses and check for other signs of danger to raise an alert.
Detection of Lateral Movement: Once a computer is infected, the malware might look around the network for other targets, like a worm. Shield 24×7‘s aiSIEM/aiXDR can quickly spot this and check other related events to warn that there might be a computer spreading malware. It can then isolate that computer to stop the spread.

DNS Protection
The Domain Name System (DNS) is like the internet’s phonebook. It helps to translate easy-to-remember website names that people use into the actual addresses that computers understand.
The Challenge
Bad actors use the DNS protocol to hide their communications and avoid getting caught. Malicious software, in particular, uses DNS to control its activities and steal data because most security systems don’t check DNS traffic.
Shield 24×7’s Solution
Shield 24×7‘s solution (aiXDR and aiSIEM) examines DNS traffic closely to spot any unusual behavior or misuse of the protocol, such as DNS Tunneling. It also uses Threat Intelligence from over 70 sources to flag domains and website addresses that are known to be risky. Plus, it works with many Firewalls to automatically block communication with these risky domains and any Command and Control (C&C) channels.
Here are some features/functionalities that combine to form DNS Protection.
- Keeps DNS systems safe by spotting and warning about attacks like DDoS Amplification and Volumetric Attacks.
- Uses smart technology to spot DDoS Attacks and suspicious Command and Control communications.
- Finds risky websites by looking for domains made with certain algorithms.
- Checks DNS traffic closely and quickly to find threats.
- Looks at DNS questions and answers right away to see if there’s a sudden increase in problems.
- Watches how network traffic behaves to catch sneaky threats.
- Finds and warns about the DN Changer trojan.

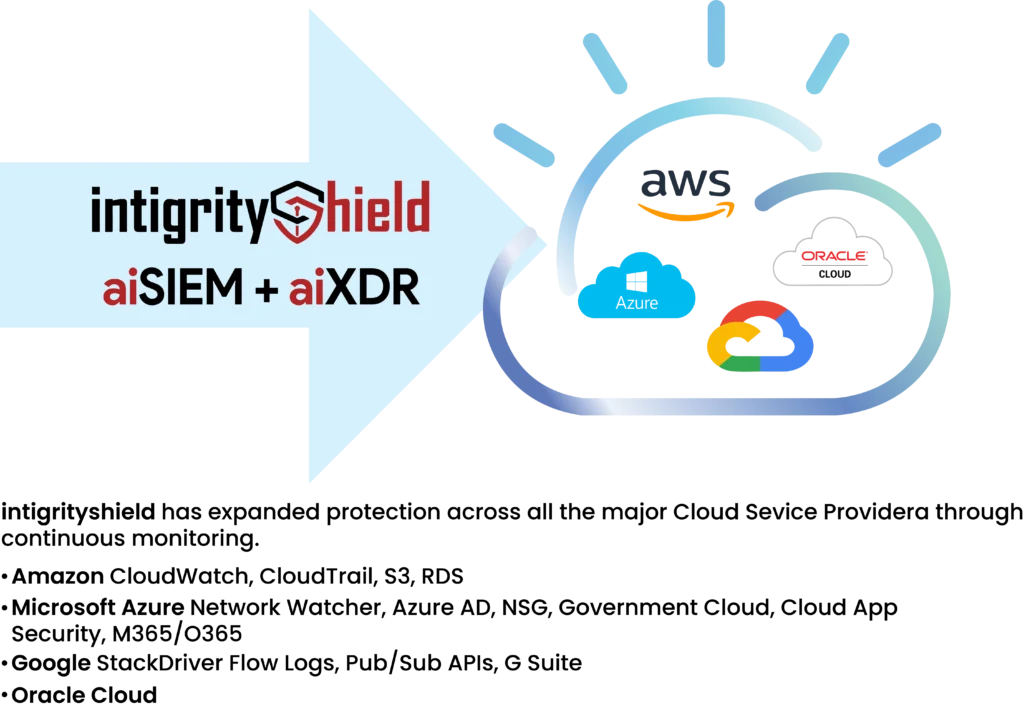
Cloud Asset Monitoring
Today, many businesses and big companies keep important stuff like apps, databases, and data files in the Cloud. So, it’s really important to keep an eye on what’s happening up there to stay safe.Lots of different people, both inside and outside the company, can get into Cloud systems. This raises the risk of someone getting hold of the wrong information or doing something they shouldn’t.And what about web apps that run from the Cloud? Aren’t they at risk of being hacked too?All these situations show why it’s so important to keep a close watch on what’s happening in the Cloud. It helps to spot problems early and keep everything safe.
Challenges
- Securing stuff in the cloud is an ongoing thing because businesses keep growing and changing. Even though there are models to help, a lot of the time, there are still gaps because people don’t understand things well enough or don’t take the right actions.
- Making sure that people only have as much access as they really need in the cloud is hard because it often means redesigning things.
- Businesses move to the cloud because it’s cheaper and easier, but they don’t always think about the risks.
- It’s important to have lots of layers of security in the cloud, but it’s hard to find one solution that covers everything, and it can be expensive.
- Most cloud security tools focus on stopping bad stuff from happening, but it’s also important to have a good system for dealing with problems when they do happen.
- If someone gets into an account with a weak password, they can mess things up and cause big problems in the cloud.
Shield 24×7’s Solutions
Shield 24×7 knows how important it is to keep an eye on things stored in the cloud to keep a business safe. They use different tools like firewalls, threat intelligence, and detection systems to see what’s going on and put it all in one easy-to-use place. They look out for things like strange connections, data moving in or out, and unusual behavior that could be a sign of trouble.
Here are some examples of the kinds of problems Shield 24×7‘s products can spot in the cloud:
- Compromised Credential
- Brute-Force Attack
- Blacklisted Site Access
- SQL Injection
- Potential Ransomware
- Zero-Day Malware
- DDoS Attacks
- Trojan Activity
- Cross-site Scripting
- DNS Tunneling Attack