Immediate Response, Verified Threats, Adaptive Controls.
IntigrityShield Open Threat Management Platform
IntigrityShield’s OTM Platform maximizes the utilization of data and insights from diverse digital assets. By employing machine learning-based behavioral analytics and AI-driven decision-making, it proactively and confidently identifies and eliminates only validated cybersecurity threats.
Challenges of Siloed Security Solutions:
- Redundant threats and alerts leading to alert fatigue
- Insufficient data points for precise threat detection
- Operational complexity with multiple dashboards across different tools and platforms
- Elevated expenses for integration, support, and maintenance
IntigrityShield’s Open Threat Management Platform is designed holistically with a 360° perspective on cybersecurity, eliminating the challenges of redundancy and disparities often found in bolt-on siloed solutions.
Real-time Processing with Swift Efficiency
Gain actionable intelligence with real-time processing speed using Big/Fast Data technology powered by in-memory computing.
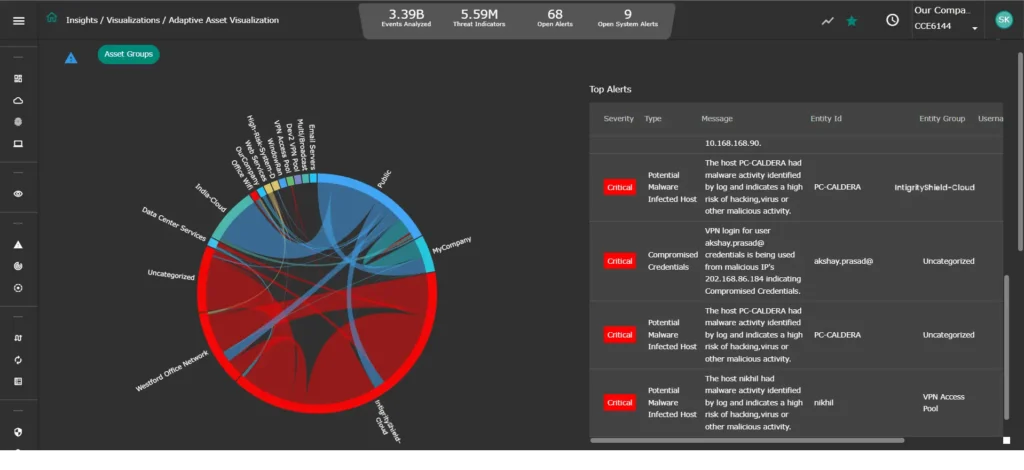
Integrated Correlation Utilizing Behavioral Patterns
Utilize user, entity, and network behavior analytics and anomalies to shape event correlation and generate dependable Threat Indicators.
Dynamic threat models for analyzing attacks
Utilize AI-driven computing to develop threat models that reflect attack techniques and tactics described in the MITRE ATT&CK Framework.
By harnessing advanced technologies, the platform incorporates state-of-the-art cyber threat detection techniques, visualization, remediation, and reporting, achieving a significant 75%-90% reduction in both capital and operational expenditures (Capex and Opex).
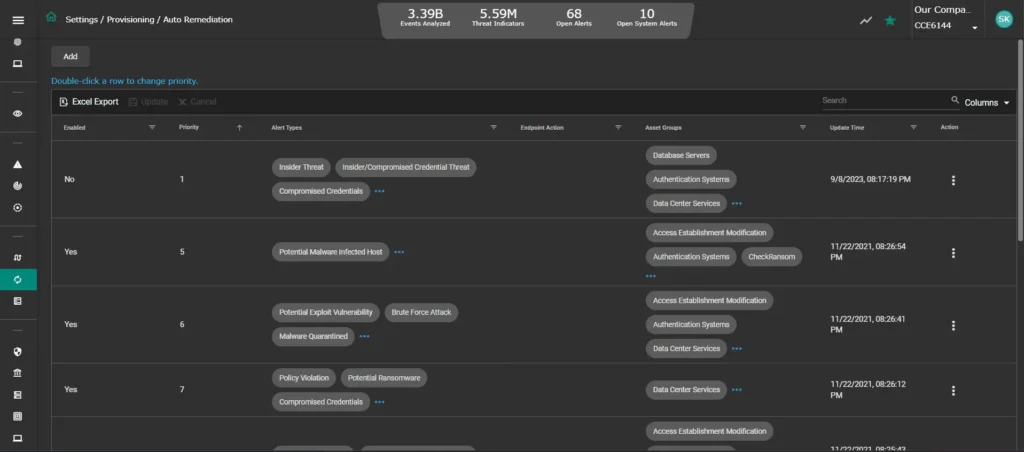
Intigrityshield’s Open Threat Management Platform strikes a fine balance by integrating automation, visibility, insights, and customizable controls, OTM enhances analytics efficiency, minimizes time-to-detection and time-to-remediation, and implements control mechanisms to enforce network policies, including micro-segmentation and user-defined alerts.
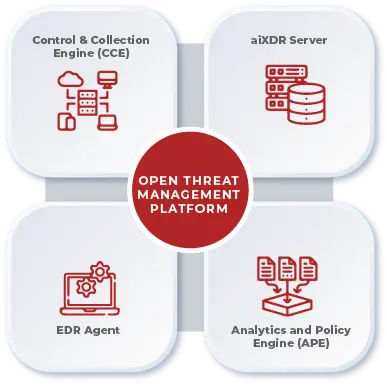
IntigrityShield OTM Key Components:
Control & Collection Engine (CCE):
The CCE coordinates event and network traffic data collection across enterprise and cloud assets. It employs intelligent detection to enrich structured and unstructured data before securely routing it to the OTM core.
EDR Agent:
Installed on each endpoint, this lightweight agent gathers detailed information on applications, processes, file events, executables, user access, and telemetry. It also enforces threat containment and elimination based on remediation policies.
Analytics and Policy Engine (APE):
At the heart of OTM, the APE processes real-time, high-volume data, incorporating threat intelligence, behavioral anomalies, historical context, and vulnerability scan results into dynamic threat models. Actionable AI and ML correlations enable automated or minimally intervened remediation routes for threat containment.
aiXDR Server:
The aiXDR Server orchestrates data collection across multiple tenants in a multi-tenant environment and delegates specific instructions to aiXDR agents communicating with the APE.
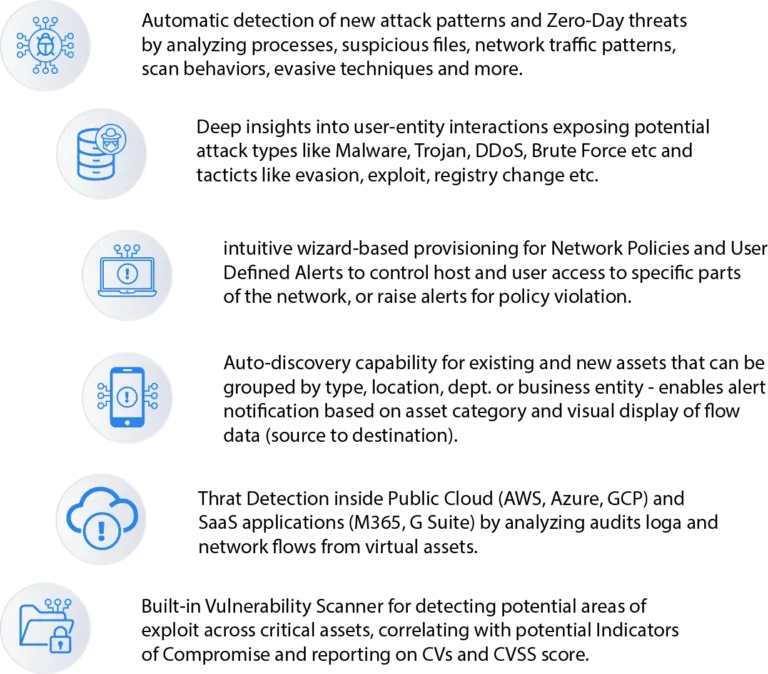
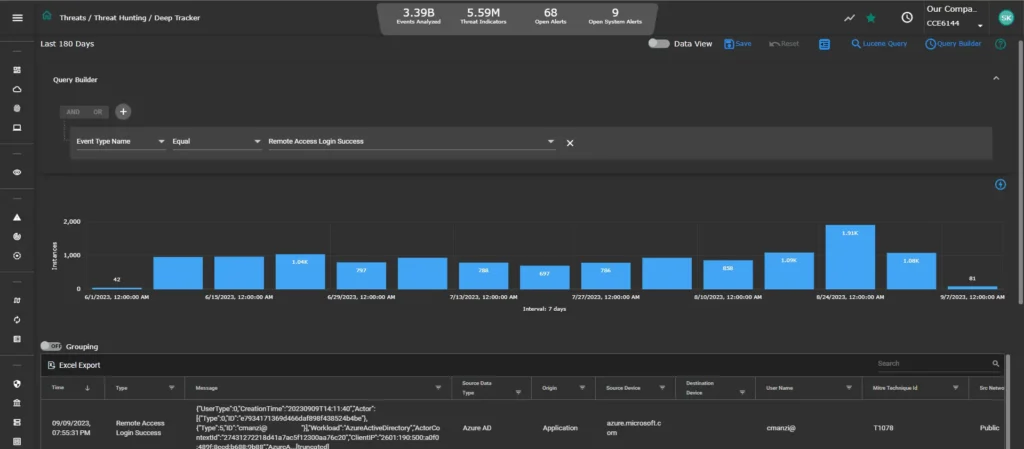
Threat Hunting with Deep Tracker
Delve into correlated threat indicators analyzed via dynamic threat models, regardless of their source (network, host, device, ML). Explore detailed event data including Event Type, Source, Host, Destination, User Name, synthesized in an accessible format for in-depth investigation.