Transformative Analytics, Comprehensive Security with aiSIEM
Advanced Threat Detection and Response
Secure all your digital assets, personnel, and network continuously at a reduced cost. Utilize real-time advanced threat detection and automated remediation powered by Machine Learning and Artificial Intelligence. Prevent breaches and maintain business continuity affordably!
Challenges of Traditional SIEM Solutions:
- Generic correlation rules leading to high rates of false positives and negatives.
- Heavy reliance on static data (event logs) missing critical indicators for early threat detection and response.
- Lack of behavioral analytics incorporating user identity, network flows, and applications, resulting in incomplete contextual alerts.
- Inadequate utilization of threat intelligence data for enriched analysis, allowing undetected malware to evade detection.
Shield 24x7's aiSIEM adopts a fundamentally different approach to cybersecurity, bypassing the pitfalls of traditional SIEM systems and enabling enterprises to effectively tackle emerging threat vectors, techniques, and tactics.
Continuous Compliance - On Demand and At Scale
Stay up-to-date and informed with regulatory compliance checks and balances at all times, even as your business grows with users, assets, and digital footprint.
Operational Efficiencies in Threat Detection
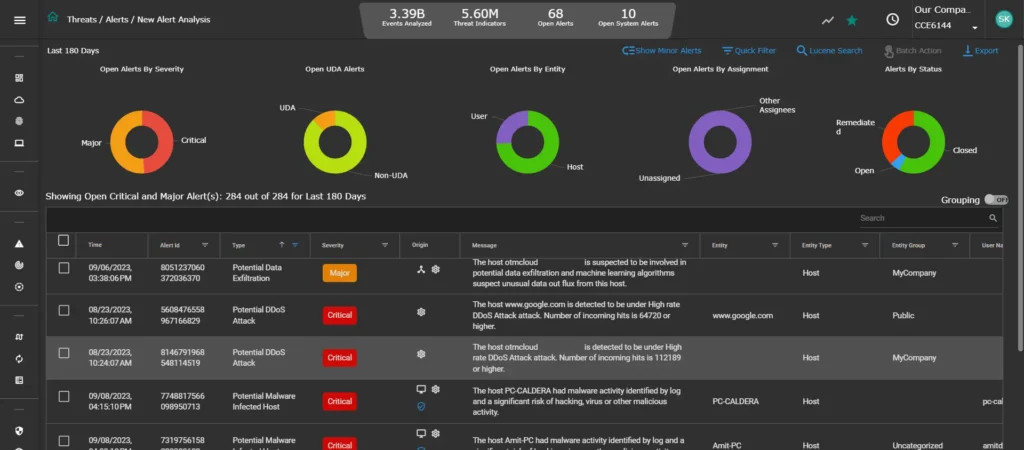
Significantly reduce operational burdens with optimized analytics and automation, ensuring you receive only the alerts that matter – eliminating false positives.
Qualitatively Enhanced Outcomes
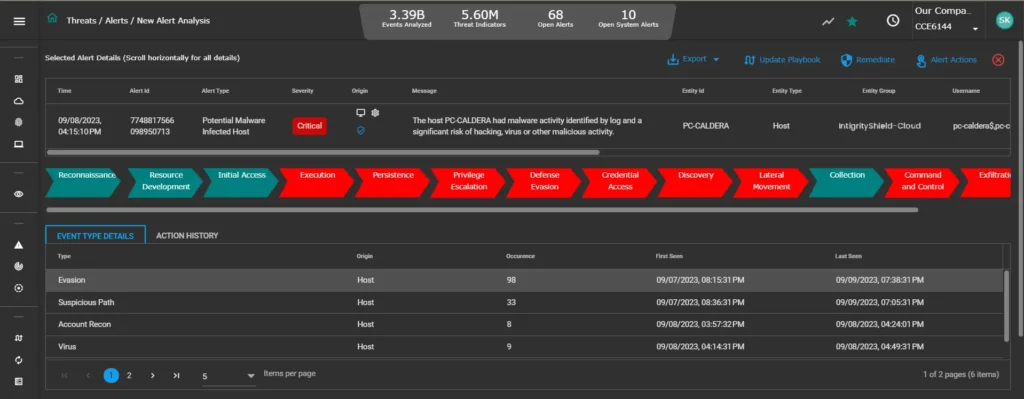
Gain confidence from alerts supported by validated Indicators of Compromise (IOCs) and prompt manual or automated responses.
Detect and neutralize both known and unknown threats across all your digital assets—whether on-premises, in the cloud, or remote—before they escalate into major incidents.
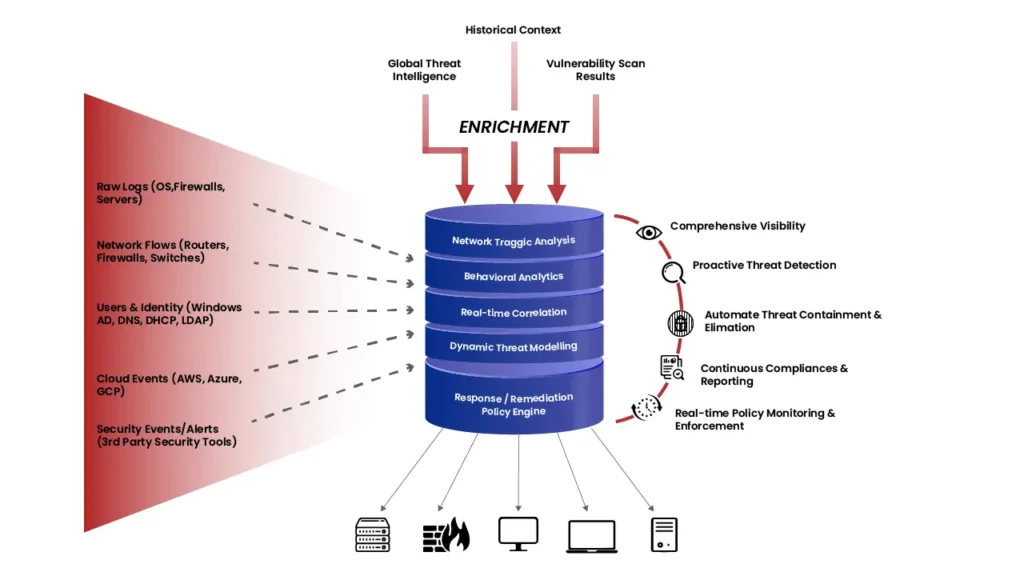
A robust security posture necessitates extensive visibility into cyber threats, exploits, and attacks targeting your IT assets. Shield 24×7 aiSIEM integrates validated threat indicators, correlated events, and network traffic flows, enhanced with threat intelligence, behavioral anomalies, historical context, and vulnerability scan findings. This results in highly effective and cohesive alerts, minimizing alert fatigue, and enabling timely semi-automated or automated responses.
React swiftly. Minimize impact. Control risk.